YubiKey 5 Nano Two Factor Authentication To Protect It self Again From The Risks of Cybersecurity
The proactive steps using YubiKey 5 Nano Two Factor Authentication are needed to be taken to ensure adequate protection for a business. The size of a business is affecting the security measures taken. The relevant procedures should be implemented to protect itself again from the risks of cybersecurity.
In 2004, the cyber essentials scheme was launched by the BIS, highlight the implementation of the control that will be used to help the IT system’s security, and migrate the risks of cybersecurity.
YubiKey 5 Nano Two Factor Authentication effective controls are crucial to be ensured the identify information and assets that are vulnerable to the challenge of cybersecurity. The safeguard for a business can be taken by understanding this Cyber Essential Scheme

YubiKey 5 Nano Two Factor Security Key Secure Configuration Using YubiKey
 |
|
The network such as internet gateway and boundary firewall should be noticed to protect the applications, information, devices, and system against unauthorized access. If this important thing is ignored, the system may be easily accessed if not use YubiKey 5 NanoTwo Factor Security Key. By regulating outbound and inbound network traffic, a boundary firewall works as a defense. There are several things recommended by the scheme. The firewall password is not the default option and should be strong. Each rule should allow the firewall to be passed by network traffic should be approached by an authorized individual and should be documented. Routinely unapproved and susceptible services should be locked to default at the boundary. There should be always updated of the firewall so that the out-of-date can be deleted. And the dashboard should be impossible to be accessed to manage the firewall. |
|
There must be a configuration for the device that is connected to the network that they can only give the service required and never give access to surplus systems or networks. The YubiKey 5 NanoTwo Factor Security Key can simplify this. Cyber attackers can get a route to gain access easily to get the information of the network device because of the default applications or settings on the device. It is recommended to employ some basic control when the network device installing. The unneeded user account should be deleted, the password should be strong, and not use the default installation. You should disable or remove redundant software. Autorun or another software setting should be disabled so that you can prevent them being active. The purpose is to prevent their being active when you are accessing network folders and removable storage. The firewall is usually installed on a computer and is regarded as part of OS so that you need to use YubiKey 5 NanoTwo Factor Security Key. |
Using YubiKey 5 Nano Two Factor Authentication For Malware ProtectionIf a computer is connecting to the internet, it means that there is should be an installation of malware protection software to protect against viruses, spyware, and worms, and other kinds of malware that work an unauthorized performs. These malware can be transmitted easily because several of means such as files on storage media, emails, or websites, malware protection, and YubiKey 5 Nano Two Factor Authentication will protect your computers against cyber attacks that are possible. The protection software must be set to automatically scan files and always kept up to date. It is recommended for the use of more established malware protection for servers and laptops, desktop PCs, devices such as smartphones and tablets are also needed malware protection. |
YubiKey 5 Nano Two Factor Authentication For Understanding Patch ManagementEvery device has a risk to be attacked by the weakness contained in software that run by such device we connecting to a network if not using YubiKey 5 Nano Two Factor Authentication. Software producers will be always monitored release and flaws software updates that are known as patches. The patch management process should be formalized so that there will be an effective monitoring and an efficient installation, creating a strategy that breaks down the patches’ type that should be applied to every system or software and what time. If there an update available of the software, install it as soon s possible. For patches’ security, the installation that recommended is is within 14 days from the release or as soon as possible, it is better to use YubiKey 5 Nano Two Factor Authentication. |

Specifications of YubiKey 5 Nano
|
USB Type |
USB-A |
|
|
NFC-Enabled |
No |
|
|
Authentication Methods |
Passwordless, Strong Two Factor, Strong Multi-Factor |
|
|
Identity & Access Management |
AWS Identity and Access Management (IAM), Centrify, Duo Security, Google Cloud Identity, Idaptive, Microsoft Active Directory, Microsoft Azure AD, Okta, Ping Identity |
|
|
Productivity & Communication |
Google Account, Microsoft account, Salesforce.com |
|
|
Password Managers |
1Password, Dashlane Premium, Keeper®, LastPass Premium |
|
| Operating Temperatures |
0 °C - 40 °C (32 °F - 104 °F) | |
| Storage Temperatures | -20 °C - 85 °C (-4 °F - 185 °F) |
|
Function |
WebAuthn, FIDO2 CTAP1, FIDO2 CTAP2, Universal 2nd Factor (U2F), Smart card (PIV-compatible), Yubico OTP, OATH – HOTP (Event), OATH – TOTP (Time), Open PGP, Secure Static Password |
|
|
Certifications |
FIDO 2 Certified, FIDO Universal 2nd Factor (U2F) Certified |
|
|
Cryptographic Specifications |
RSA 2048, RSA 4096 (PGP), ECC p256, ECC p384 |
|
|
Design & Durability |
Water Resistant, Crush Resistant, No Batteries Required, No Moving Parts |
|
|
Device Type |
FIDO HID Device, CCID Smart Card, HID Keyboard |
|
|
Manufacturing |
Made in USA and Sweden |
|
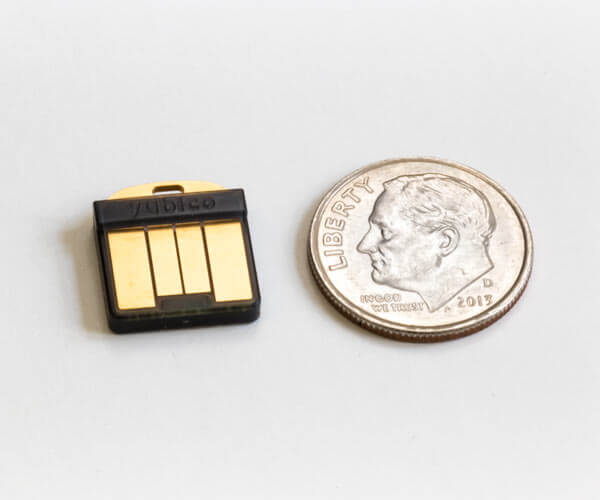
| Dimensions | 12mm x 13mm x 3.1mm | |
| Weight | 1g |
YubiKey 5 NanoTwo Factor Security Key Access Control for Users
|
An application, network, or device requires a minimum level of access, it is should be allowed by the users’ accounts. Special privileges to administer control are required by users should belong to individuals. The scheme suggests several things to help control access. The initiation of each user account must be approved in a formal process. There should be a limitation for users with special rights and their detail should be kept and documented in a secure location. YubiKey 5 NanoTwo Factor Security Key each administrative account must serve the administrative purpose for which It was created. YubiKey 5 NanoTwo Factor Security Key Creating Strong PasswordsThe first line for the defense is passwords. Therefore, it should be created as strong as possible. You can include more than three words, lower and upper cases, symbols, and numbers, try to avoid making common passwords to avoid the possibility of cyber hacks. Avoid using your date of birth, name of your family member, your name, or the name of the current partner, favorite holiday, number sequences, significant dates, and places of birth and use the YubiKey 5 NanoTwo Factor Security Key as the superior security. A cracked password can easily give a large amount of information access to cyber attackers. A brief password policy that sets out some of the top tips can help to tell that a strong password is important to employees. Using YubiKey 5 Nano Two Factor AuthenticationTo protect yourself against data theft or cyber- attack, YubiKey 5 Nano Two Factor Authentication is the perfect method. This security key, at its core, is a defense against human strategy and phishing, after all, you can’t be tricked into giving out your credentials when you don’t know what they are. An intuitive and simple authentication is provided by the YubiKey 5 Nano Two Factor Authentication. Users will discover that it is very easy to use and ensuring rapid adoption. Than SMS based authentication or OTP, the speed of this smart-small device is 4x faster. It does not require network connectivity or battery and always make the authentication accessible. |
|
|
Works on
More YubiKey
Ready to get started?
Call us now to get free quotation about your customize project
Call us on